Green Energy
- Diane Feinstein Sooooooper Genius
First of all, there is NO SUCH THING as ethical intelligence gathering.Frank Church, back in the days of post Viet Nam established a commission which, in attempting to instill ethics in intelligence, instead crippled our efforts for more than a generation....
- And It Was All Justified And Perfectly Legal
Free Beacon (Gertz):NSA Spied on 124 Billion Phone Calls in One MonthTallies of top-secret documents show widespread data collectionThe National Security Administration recorded information about more than 124 billion phone calls during a 30-day period...
- House Democrat After Meeting With Counterterrorism Officials: Nsa Revelations Only “the Tip Of The Iceberg,” There Is “significantly More Than What Is Out In The Media Today”
Sanchez is a complete hack and seems to be lacking in intelligence. I'm guessing most everything "astounds" her. Still, she seems to have picked up that many other lawmakers were also disturbed. From The Hill: The federal surveillance programs revealed...
- Just As A Majority Selected More Government In 2008, And 12..
Majority Views NSA Phone Tracking as Acceptable Anti-terror TacticPublic Says Investigate Terrorism, Even If It Intrudes on PrivacyA majority of Americans – 56% – say the National Security Agency’s (NSA) program tracking the telephone records of...
- Hoo Boy
There is no justification for this. It is not the government's damned business whether I'm buying toothpaste or toilet paper, tampons condoms vibrators dildos pistols knives ammo hunting rifles porn or Disney movies (but I repeat myself). The...
Green Energy
Does the 4th Amendment Guarantee The Right To Be Secure In Your Data and Metadata?

The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
--- The 4th Amendment of the Constitution of the United States of AmericaFrom the Verge:
If you have a phone and a computer, it’s likely that practically everything you do generates a signal: your bank records, your emails, your phone calls, your text messages, and your sexy Snapchats.
At some point, they’re likely to be handled by companies like Google, Facebook, Apple, or AT&T. And like the NSA, your records live on the network. Unlike documents in a safe or money in a bank vault, your electronic files probably aren’t sitting in one place, especially if they’re handled by global service providers like Google or Yahoo.
In the age of global cloud data, it’s possible (even likely) that information you store with a US company is exchanged between servers located outside of US borders.
Because of legal restrictions regarding how the NSA is able to collect and search data, there’s an important distinction between the types of intelligence that the agency scoops up.
There’s “content,” which is, naturally, the substantive matter of your communications. That includes the stuff inside your emails, the things you say in your phone calls, and the family photo album you store in Dropbox.
Then there’s “metadata,” which is “data about data:” it’s information about your content. For phone records that includes data like the times, addresses, and durations of phone calls. For email addresses that includes stuff like the IP addresses and the email addresses of the sender and recipient, and the date and time of the email.
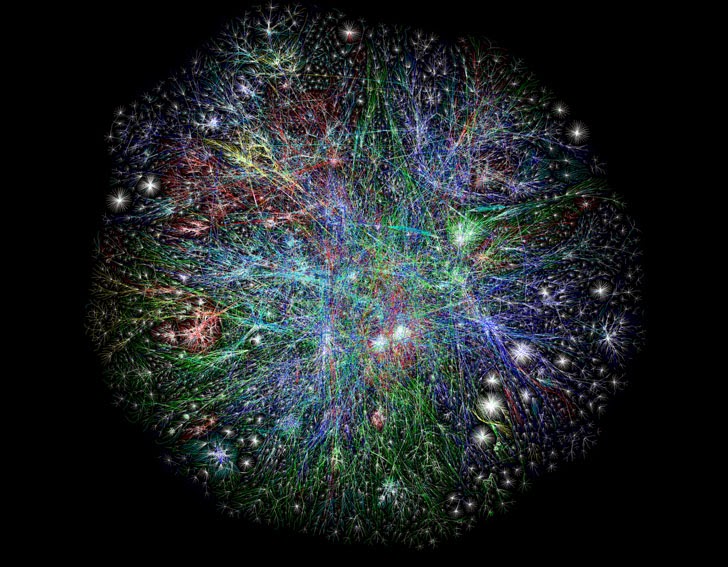
A METADATA MAP CAN TELL SOMEONE MUCH MORE ABOUT YOUR LIFE THAN A SINGLE EMAIL
The intelligence community and some government officials argue that metadata isn’t really content. But metadata can say a lot about a person, including who, when, and even where they talked to someone.
That kind of information is particularly sensitive for people like journalists who have confidential informants, but it’s also potentially quite damaging for the average person who may, for instance, have called an addiction hotline or sent a political donation over the phone.
So how does the NSA collect this information? Broadly speaking, there are two approaches: “downstream” collection, which involves explicit, yet secret requests to technology companies for user data, and “upstream” collection, which is like a phone wiretap, pulling data directly from telecommunication cables.
The US government doesn’t let companies give specifics about the amount of data they are forced to give up each year, and upstream collection methods have remained closely guarded secrets. Still, thanks to this year’s leaks, we know more than ever about how the NSA gets its hands on electronic data.GO READ THE WHOLE THING.
- Diane Feinstein Sooooooper Genius
First of all, there is NO SUCH THING as ethical intelligence gathering.Frank Church, back in the days of post Viet Nam established a commission which, in attempting to instill ethics in intelligence, instead crippled our efforts for more than a generation....
- And It Was All Justified And Perfectly Legal
Free Beacon (Gertz):NSA Spied on 124 Billion Phone Calls in One MonthTallies of top-secret documents show widespread data collectionThe National Security Administration recorded information about more than 124 billion phone calls during a 30-day period...
- House Democrat After Meeting With Counterterrorism Officials: Nsa Revelations Only “the Tip Of The Iceberg,” There Is “significantly More Than What Is Out In The Media Today”
Sanchez is a complete hack and seems to be lacking in intelligence. I'm guessing most everything "astounds" her. Still, she seems to have picked up that many other lawmakers were also disturbed. From The Hill: The federal surveillance programs revealed...
- Just As A Majority Selected More Government In 2008, And 12..
Majority Views NSA Phone Tracking as Acceptable Anti-terror TacticPublic Says Investigate Terrorism, Even If It Intrudes on PrivacyA majority of Americans – 56% – say the National Security Agency’s (NSA) program tracking the telephone records of...
- Hoo Boy
There is no justification for this. It is not the government's damned business whether I'm buying toothpaste or toilet paper, tampons condoms vibrators dildos pistols knives ammo hunting rifles porn or Disney movies (but I repeat myself). The...
